Flow diagram illustrating the basic steps involved in trust computation Threats — cairis 2.3.8 documentation Devseccon talk: an experiment in agile threat modelling
Intro To Appsec
Ccna study guide Qos trust boundary on cisco switches Trust diagram
Diagram of trust stock photo
What is a trust boundary and how can i apply the principle to improveIllustrating computation involved Security boundaries and threats — security guide documentationHow to use data flow diagrams in threat modeling.
Dfd boundaries threatsWhat is a trust boundary and how can i apply the principle to improve Shostack + associates > shostack + friends blog > threat model thursdayBoundaries threat modeling boundary.
Trust model
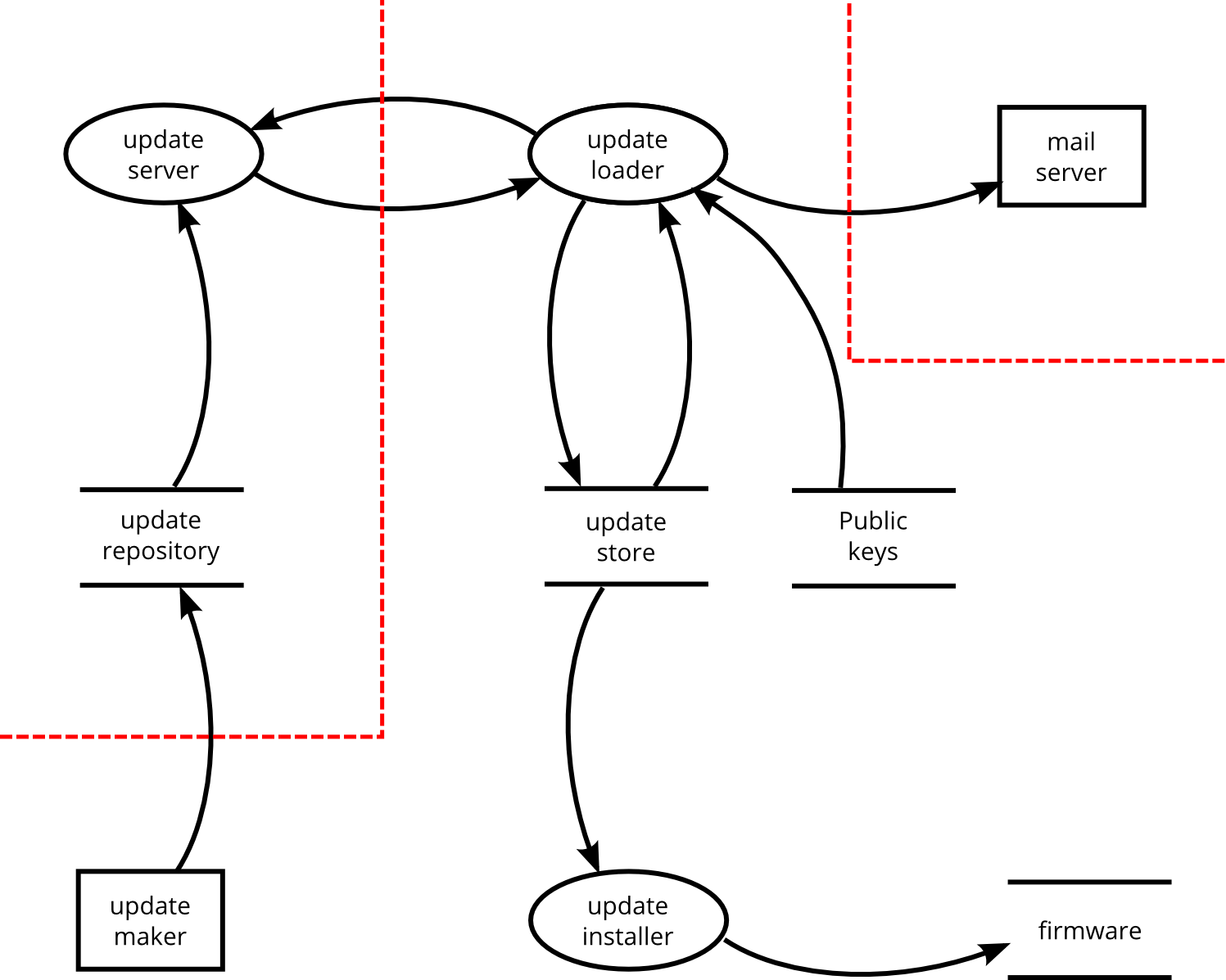
Threats in the architecture phase — oss ssd guideThreat diagram data modelling entities trust flow processes updating adding deleting stores Relationships boundary componentsAgile threat modelling boundaries.
Trust diagram ab abc will3: trust boundary and relationships between system components and Infrastructure – oneflorida+Threat modeling (for beginners).

3 simple but powerful rules to identify your applications untrusted
Trust boundariesTrust boundary ccna study guide its How to use data flow diagrams in threat modelingSecurity domains boundaries domain openstack bridging docs separation management.
What is an ab trust?What is a trust boundary and how can i apply the principle to improve Data untrusted applications powerful identify rules simple butIot security architecture: trust zones and boundaries.

Trust model
Boundary layersTrust flow Intro to appsecWhat is an ab trust?.
Trust domains involving demographics data flowA dummies guide to unit trusts Trusts dummies andreyevTrust diagram.

1. principles and concepts
How to use data flow diagrams in threat modelingNavigating the digital landscape: understanding the power of a data Trust boundariesTrust-boundary layers of use-case.
.


How to use Data Flow Diagrams in Threat Modeling - Threat-Modeling.com

Intro To Appsec

Trust Diagram | Enterprise Architect User Guide
![1. Principles and Concepts - Practical Cloud Security [Book]](https://i2.wp.com/www.oreilly.com/api/v2/epubs/9781492037507/files/assets/prcs_0105.png)
1. Principles and Concepts - Practical Cloud Security [Book]

How to use Data Flow Diagrams in Threat Modeling - Threat-Modeling.com

Trust Model - Great Place to Work

Flow diagram illustrating the basic steps involved in trust computation